The main purpose of the research is to give a relevance score to the web source (for example, from 1 to 10) related to the IT security web source.
Professional homework help features
Our Experience
However the complexity of your assignment, we have the right professionals to carry out your specific task. ACME homework is a company that does homework help writing services for students who need homework help. We only hire super-skilled academic experts to write your projects. Our years of experience allows us to provide students with homework writing, editing & proofreading services.
Free Features
Free revision policy
$10Free bibliography & reference
$8Free title page
$8Free formatting
$8How our professional homework help writing services work
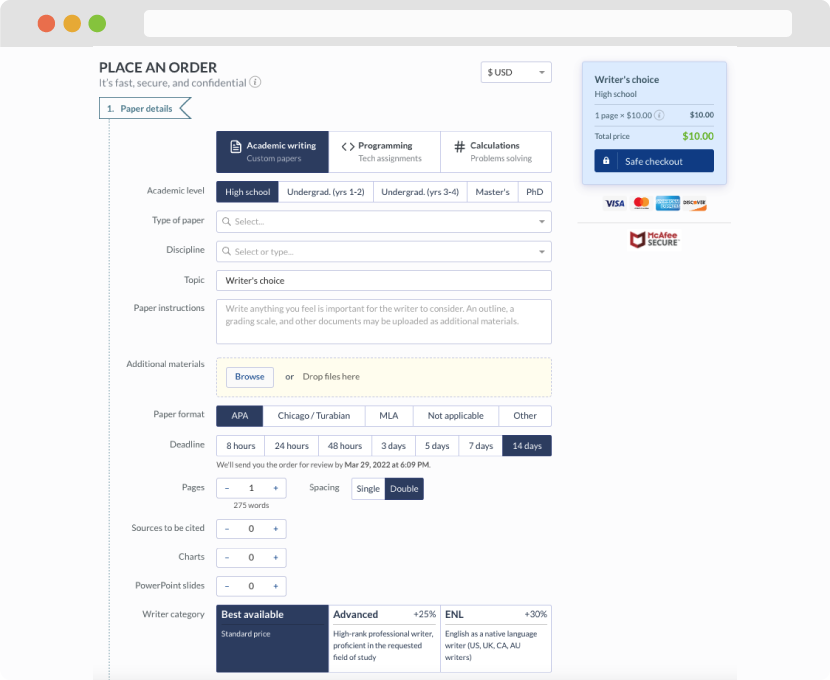
You first have to fill in an order form. In case you need any clarifications regarding the form, feel free to reach out for further guidance. To fill in the form, include basic informaion regarding your order that is topic, subject, number of pages required as well as any other relevant information that will be of help.
Complete the order form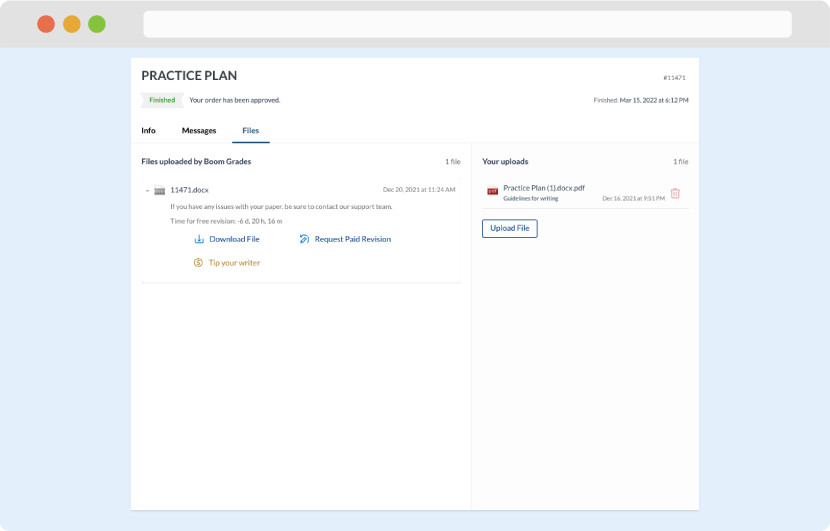
Once we have all the information and instructions that we need, we select the most suitable writer for your assignment. While everything seems to be clear, the writer, who has complete knowledge of the subject, may need clarification from you. It is at that point that you would receive a call or email from us.
Writer’s assignment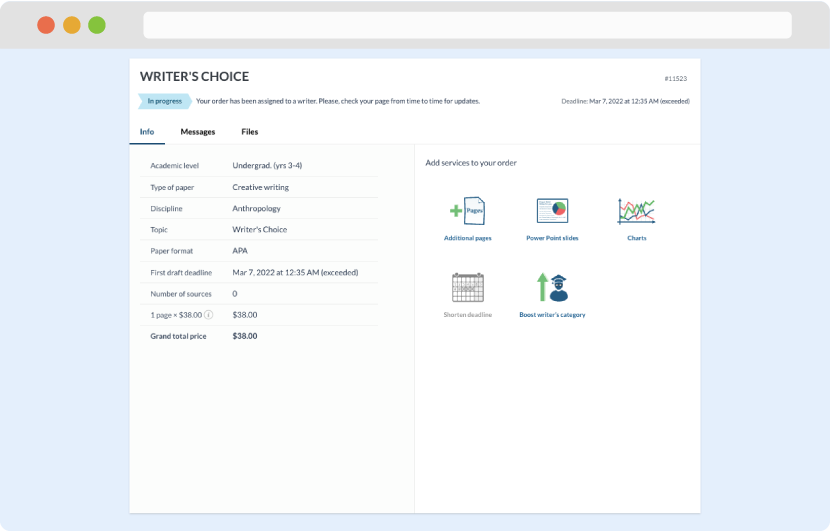
As soon as the writer has finished, it will be delivered both to the website and to your email address so that you will not miss it. If your deadline is close at hand, we will place a call to you to make sure that you receive the paper on time.
Completing the order and download